The Hard Truth: Software, a Decisive Warfighting Domain
The militaries that will dominate future conflicts aren’t just buying better jets or tanks. They’re rewriting the rules of engagement through software. Consider these facts:
1. The Cost of Falling Behind
-
-
-
- A single unpatched vulnerability in a legacy software allowed simulated Chinese cyber penetration in 78 seconds during 2023 Northern Edge exercises
- From trials and defense exercises of a major military alliance, it was estimated that 60% of C2 systems cannot share real-time data – creating 8 to12 minute decision delays against peer adversaries
-
-
2. The USD 12 Billion Pivot
The DoD’s FY2025 budget allocates USD 12.1 Billion specifically for:
-
-
-
- AI/ML combat systems (Project Maven NextGen)
- Zero-trust infrastructure (Thunderdome expansion)
- Hypersonic battle management (HYBRID software stack)
-
-
This isn’t IT modernization – it’s strategic survival.
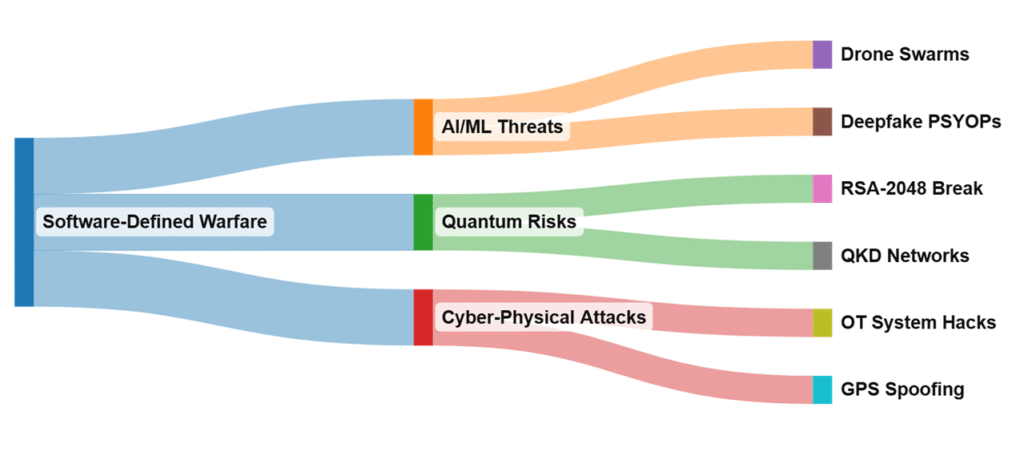
Military Software-Defined Kill Chain
Three Battlefronts Where Military Software Will Decide Superiority
1. AI/ML: The New Arms Race (Over USD 8 Billion Opportunity)
The Stark Divide
-
-
- Leaders: US/UK AI-enabled EW systems now jam 140% more effectively than legacy platforms
- Laggards: Majority of European militaries still use conventional logistics planning
-
Critical Moves for 2025-2027
-
-
- Demand “Glass Box” AI– Every algorithm must explain decisions to maintain DoD Ethical AI Certification
- Hire or Acquire– Over 40% talent gap in cleared ML engineers won’t fix itself
- Pressure-Test Against China’s “AI Suicide Swarms” (PLA’s 2023 Zhuhai Airshow demo)
-
2. Cybersecurity: The Software Supply Chain is Your Weakest Link
The New Reality
-
-
- SolarWinds was just the beginning – Russian GRU’s “Fancy Bear” now targets defense CI/CD pipelines
- USD 720 million in breaches traced to unpatched operating systems
-
Immediate Actions
-
-
- Implement DISA’s “Enclave” Model – Isolate development environments
- Mandate SBOMs – A major defense contractor now requires 4-tier component tracing
- Assume Breach – NSA’s new “Controlled Failure” protocols reduce dwell time from 280 to 9 days
-
Case Example:
A Top 5 defense prime avoided USD 210 million in ransomware costs by pre-deploying quantum-resistant encryption across its fighter jet EW software line.
3. JADC2: Interoperability or Obsolescence
The Hard Numbers
-
-
- 8 seconds – Decision speed with fully integrated multi-domain software (INDOPACOM wargames)
- 12 minutes – Average delay using stovepiped systems
-
How Winners Are Adapting
-
-
- Lockheed’s Skunk Works built a Kubernetes-based combat cloud that reduced sensor-to-shooter time from minutes to seconds.
- Over-the-air updates to jets mid-mission
-
Warning:
Firms not MOSA-compliant by 2026 will lose eligibility for billion dollar contracts in CJADC2.
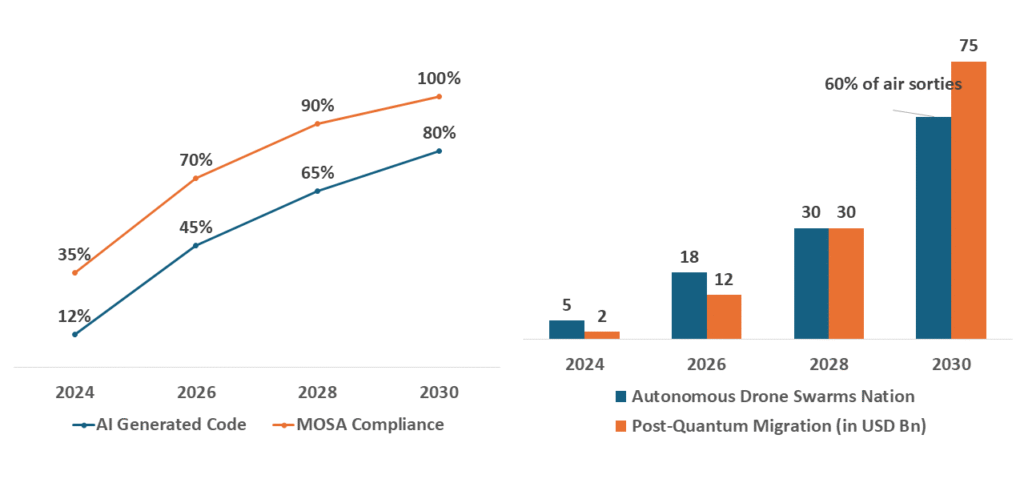
Global Military Software Adoption & Threats (2024–2030)
The CEO Agenda: Three Non-Negotiable Moves
1. Conduct a “Digital Trinity” Audit
Assess your military software position on:
-
-
- AI Readiness (≥50 certified ML models in production)
- Cyber Resilience (Zero-trust score ≥87/100 on DISA scale)
- Architecture Flexibility (MOSA compliance across ≥70% of products)
-
Our proprietary model shows only a few defense primes meet all three criteria.
2. Rewrite Your Talent Playbook
-
-
- Poach from Big Tech – Engineers from big tech firm with additional bonuses on tech clearance
- Reskill Legacy Teams – Northrop’s “Code Phoenix” retrained COBOL programmers in Rust/Julia
-
3. Build the “Digital Twin” Moonshot
-
-
- Simulating 2.1M cyberattacks/hour on missile defense software
- Boeing’s Loyal Wingman uses reinforcement learning that improves after every sortie
-
The 2030 Global Defense Software Market Revolution: A New Era of Strategic Competition
By 2028, majority of military software worldwide will be AI-generated, with the U.S. (DARPA’s AIxCC), China (PLA’s “Cognitive Warfare” platforms), and Russia (Kronstadt Group’s autonomous systems) leading the charge. This shift is democratizing advanced capabilities like AI-powered drone swarms, while commercial LLMs (like China’s ERNIE Bot) lower the barrier for cyber operations.
However, uneven adoption risks creating a “code divide” where only quantum-ready nations can secure their systems. The expiration of RSA-2048 will trigger a USD 30 billion global PQC transition race, with Europe’s PQCRYPTO Project and India’s C-DAC emerging as key players.
By 2030, autonomous software factories will dominate defense production, with China’s AI “Wingman” coders already outpacing human teams. NATO’s DIANA accelerator and India’s iDEX program aim to counterbalance this, but the real disruptors may be non-state actors – hacktivists using open-source AI tools like Stable Diffusion for deepfake psyops.
The new strategic imperative is “software interoperability alliances”: Nations that fail to standardize on MOSA-compliant, quantum-hardened systems will become vulnerable to algorithmic warfare decapitation strikes.
Your competitors are already moving. Schedule a Briefing or Get Sample to stay ahead of the curve.



